Why DORA Metrics Belong in the Risk Committee Packet
Source: IRM Navigator™ Research
The Board Issue
Boards increasingly receive dashboards showing deployment speed, incident counts, and technology uptime. What is often missing is the recognition that software delivery performance is now a primary driver of enterprise risk. Every material change to products, services, data flows, and controls is executed through software delivery pipelines.
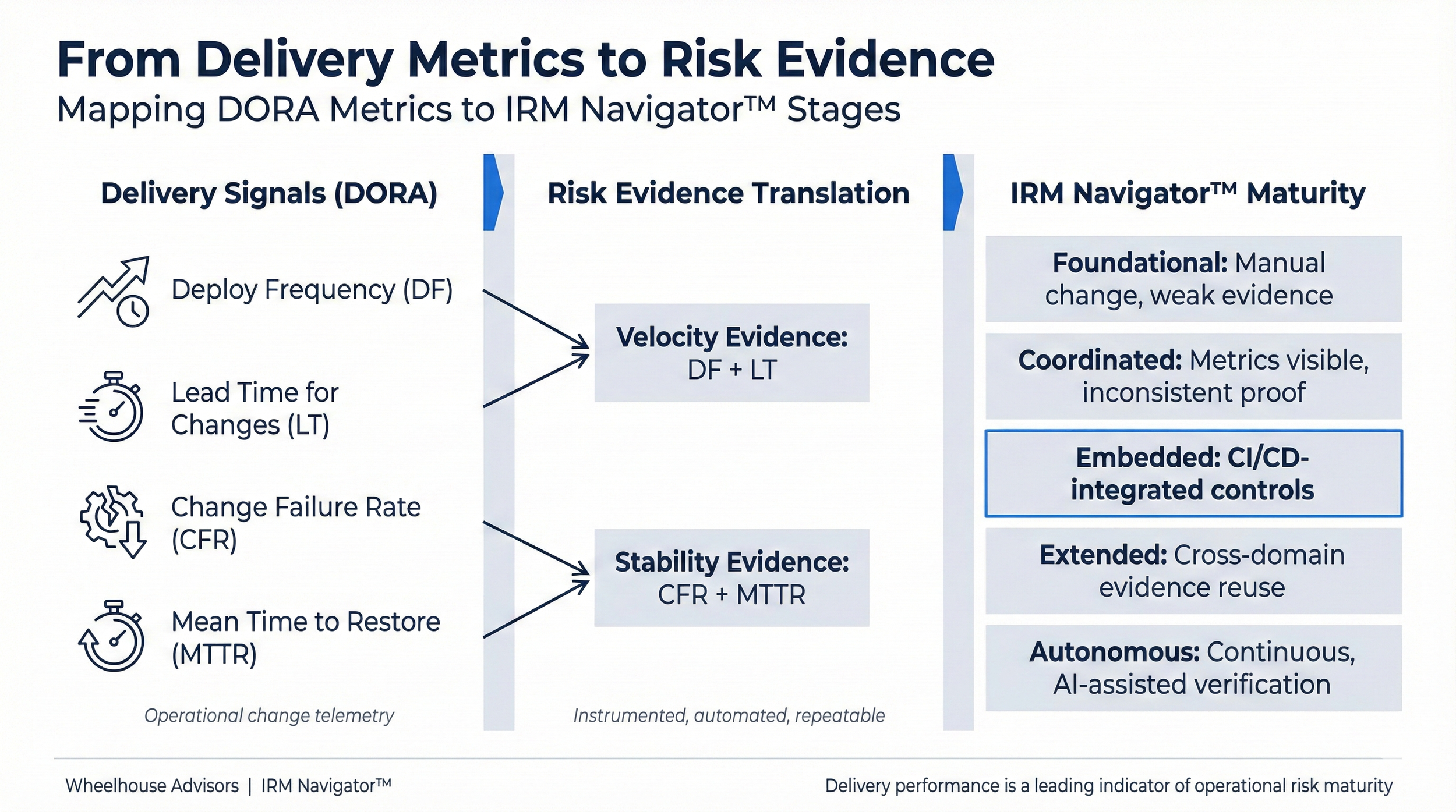
DORA metrics were created to measure delivery performance, but when viewed through an integrated risk lens, they function as early-warning indicators of change risk, operational resilience, and assurance quality. Boards that treat these metrics as engineering detail miss one of the clearest signals of whether risk controls are embedded or cosmetic.
Five Questions Directors Should Ask
Is change velocity predictable or episodic?
Consistent deploy frequency and lead time signal disciplined execution. Spikes around major releases often correlate with elevated change risk.Where do changes fail and why?
Change failure rate is not just a quality metric. It reveals systemic control weaknesses when failures cluster in specific systems, teams, or vendors.How fast can the organization recover from its own changes?
Mean time to restore is a direct measure of operational resilience. Recovery measured in days indicates fragile controls, regardless of policy strength.Is delivery telemetry reused as control evidence?
Boards should challenge whether audit and compliance teams rely on automated pipeline evidence or still request screenshots and manual attestations.What maturity stage does delivery evidence support?
Management should be able to demonstrate how delivery metrics substantiate progress along the IRM Navigator™ maturity path, not just report them in isolation.
Signals Boards Should Expect to See
Stable, repeatable trends in deploy frequency and lead time
Change failure rates tied to root-cause analysis and corrective action
Recovery times measured in minutes or hours, supported by defined restore playbooks
Automated evidence captured directly from continuous integration/continuous deployment (CI/CD) and runtime platforms
Shorter audit cycles and fewer post-implementation control findings
Next-Quarter Board Mandates
Reclassify delivery metrics as risk indicators, not IT productivity measures
Align risk appetite statements with acceptable thresholds for change failure and recovery time
Prioritize automation of evidence collection over adding new manual controls
Require management to map delivery evidence to integrated risk maturity, not siloed reports
The Board Takeaway
Organizations that can change quickly and recover safely are not simply agile. They are structurally better controlled. DORA metrics provide boards with early, objective proof of whether risk management is embedded in daily operations or deferred until audit season.
Boards that demand this evidence gain foresight into operational risk. Boards that ignore it are left reviewing incidents after value, and trust, have already been lost.
References
Forsgren, N., Humble, J., Kim, G. Accelerate: The Science of Lean Software and DevOps. IT Revolution Press, 2018.
DevOps Research and Assessment (DORA). “DORA’s software delivery performance metrics” (metrics definitions and evolution notes). DORA.dev, accessed January 2026.
Institute of Internal Auditors (IIA). Global Technology Audit Guide (GTAG): Auditing DevOps (audit perspective on CI/CD controls and evidence). IIA, latest edition.
National Institute of Standards and Technology (NIST). SP 800-53 Rev. 5: Security and Privacy Controls for Information Systems and Organizations. U.S. Department of Commerce, 2020.
Wheelhouse Advisors, The RiskTech Journal. “The Implications of DORA Starting Today: Opportunities for Integrated Risk Management to Drive Resilience.” Published January 17, 2025.
Wheelhouse Advisors, The RiskTech Journal. “Navigating the DORA Deadline: Why Integrated Risk Management Is Critical.” Published 2024.
Wheelhouse Advisors, The RiskTech Journal. “DORA’s Wide Net: More Than Just Cybersecurity for Financial Services.” Published 2024.