
Click here to access subscription content at The RTJ Bridge - The Premium Version of The RiskTech Journal
〰️
Click here to access subscription content at The RTJ Bridge - The Premium Version of The RiskTech Journal 〰️
The RiskTech Journal
The RiskTech Journal is your premier source for insights on cutting-edge risk management technologies. We deliver expert analysis, industry trends, and practical solutions to help professionals stay ahead in an ever-changing risk landscape. Join us to explore the innovations shaping the future of risk management.

When Tokens Turn Toxic: How the Salesforce Supply Chain Breach Exposed the SaaS Domino Effect
A coordinated campaign has exploited a popular integration between Salesloft, Drift, and Salesforce, resulting in unauthorized access across some of the world’s most trusted enterprises. Palo Alto Networks, Zscaler, Cloudflare, and Proofpoint have all confirmed impacts to their Salesforce environments, while Okta reported blocking the attack through network restrictions.
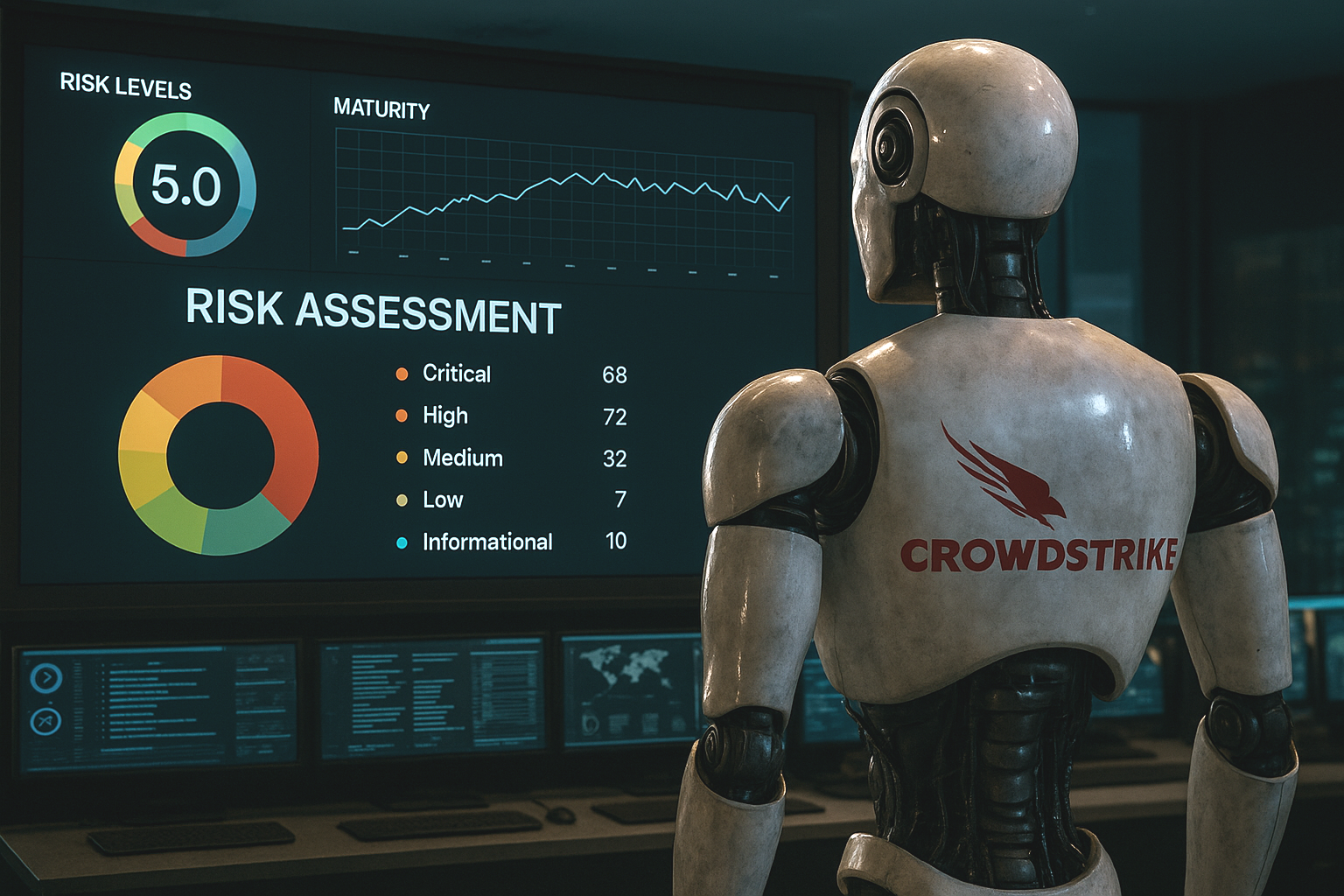
How CrowdStrike’s Agentic AI Accelerates Autonomous IRM
CrowdStrike’s launch of Charlotte AI—its agentic AI architecture now embedded within the Falcon platform—marks a decisive shift in how risk is not only detected, but addressed. With its triad of capabilities (Agentic Detection Triage, Agentic Response, and Agentic Workflows), Charlotte introduces a new operating model: one where AI systems autonomously assess, act, and learn within predefined parameters.
The implication for Integrated Risk Management (IRM) is profound. These are not just smarter alerts or faster forensics. They are machine-initiated decisions with immediate governance, compliance, and operational consequences. And that demands a new framework—one that aligns autonomous action with enterprise risk oversight.

The Coming Wave: Why AI-Fueled Cyber Crime Demands a New Layer of Risk Management
In June 2024, a ransomware attack on Synnovis—an NHS diagnostics provider—led to thousands of canceled surgeries, long-term patient harm, and yet barely registered in the headlines. A year later, an attack on Marks & Spencer, which temporarily left Percy Pig sweets and Colin the Caterpillar cakes off supermarket shelves, wiped £600 million off the company’s market cap and triggered nationwide panic.
This juxtaposition, as Misha Glenny eloquently observes in his Financial Times Weekend article, reveals something uncomfortable about both society’s perception of cyber risk and our structural ability to respond to it. But it also points to a larger and more pressing reality: AI is about to turn every cyber threat vector into a force multiplier—and the defensive tools most organizations rely on are no longer fit for purpose.
As AI matures into autonomous, agentic forms, we’re not just dealing with more attacks—we’re dealing with smarter, faster, and more scalable ones. The solution isn’t just better cybersecurity. It’s Integrated Risk Management (IRM)—and it must evolve as rapidly as the threat landscape.

Where Autonomous IRM Begins—And Where It Must Go Next
The Quiet Rise of Autonomous IRM—From the Middle Out
Autonomous IRM is no longer theoretical. AI-powered platforms are starting to deliver tangible value: agentic systems that simulate attacker behavior, validate control effectiveness, and recommend mitigation actions—often autonomously.
The June 5 announcement from Tuskira, integrating directly with ServiceNow’s Vulnerability Response and SecOps modules, is a prime example. By embedding simulation-backed scoring and posture-aware mitigation into operational workflows, Tuskira is delivering intelligence in real time.
But there’s something missing: the announcement doesn’t mention Integrated Risk Management (IRM) at all.
That silence is a signal. Tuskira operates in what Wheelhouse Advisors defines as Layer 3: Intelligence & Validation—the middle of the risk architecture. And while this layer is where automation is gaining traction, it’s also where many organizations are managing in isolation, without input from either end of the enterprise risk stack.

Beyond the Firewall - Why Integrated Risk Management Is the Missing Layer in Cyber Defense
The recent revelation that Marks & Spencer—one of Britain’s most iconic retailers—suffered a cyberattack that could cost it up to £300 million in annual operating profit is a reminder that no amount of cybersecurity spending can fully inoculate a company from human error. The attack, reportedly traced to a third-party vendor and facilitated by social engineering, underscores a hard truth: cybersecurity is necessary, but not sufficient.
Despite boosting its cyber investment by 75% and quadrupling its team over the past two years, M&S was not spared. Nor were other well-known retailers like Harrods and the Co-op grocery group. These incidents reflect a deeper problem in the digital defense playbook—one that requires a broader, integrated approach to risk.

From Code to Conduct: UK Cyber Mandate and Tech Disruption Signal a Governance Reckoning
Two significant announcements this week—one from the UK government and the other from Deloitte—highlight a rapidly converging future in which cybersecurity, advanced technology, and corporate governance are no longer siloed concerns but integrated imperatives for the boardroom. While distinct in origin and focus, both developments send a clear signal: the pressure on executive leaders to govern technology risks with discipline, foresight, and accountability is mounting.

When Encryption Isn't Enough—A Sidewalk Interview and a Global Wake-Up Call
I was in Washington, D.C., when the story broke. Reports surfaced that U.S. officials had used Signal—a consumer-grade encrypted messaging app—to coordinate sensitive military operations in Yemen. I was finishing a dinner meeting after a full day of engagements when my phone rang. It was the BBC reaching out for immediate commentary on a fast-developing national security story.

What Happens When Risk Protocols Fail - Lessons from the Signal App Incident
When BBC News investigated a recent national security communications breach, they reached out to Wheelhouse Advisors for expert analysis. The incident highlighted a growing risk not just for governments—but for every organization managing sensitive information in a digital world.

HIPAA 2.0 — How Risk Management Evolves Under HIPAA’s Cybersecurity Overhaul
In the face of escalating cyber threats, the U.S. healthcare sector is on the brink of its most dramatic regulatory transformation in more than a decade. The Department of Health and Human Services’ recent Notice of Proposed Rulemaking (NPRM) for the HIPAA Security Rule doesn’t just update a long-standing framework—it signals a revolutionary shift in how organizations must guard patient data. The stakes are higher than ever, with compliance costs set to soar and the consequences of non-compliance more severe than ever imagined.
Security Complexity Is Strangling Your Bottom Line—IRM Platforms Can Save It
By now, it’s obvious: complexity has become the Achilles’ heel of cybersecurity and enterprise risk management (ERM). In a recent study from the IBM Institute for Business Value—Capturing the Cybersecurity Dividend: How Security Platforms Generate Business Value—researchers found that companies juggle an average of 83 different security solutions, sourced from 29 distinct vendors. Beyond the technology overload lies a crucial lesson for risk leaders: more point solutions do not necessarily translate into better protection.
