
The RTJ Bridge is the new premium version of The RiskTech Journal, delivering fast-moving, strategically relevant insights for risk leaders navigating today’s digital business landscape.
Designed as the link between editorial commentary and in-depth research, The RTJ Bridge offers exclusive access to:
High-frequency insight notes on market shifts, regulatory signals, and emerging technologies
Executive briefings and editorial series including “The Risk Ignored”
Strategic previews of IRM Navigator™ research, including upcoming Risk Landscape Reports
Whether you're monitoring vendor moves, tracking governance shifts, or preparing for regulatory disruption, The RTJ Bridge equips you with actionable foresight.
The RTJ Bridge - The Premium Version of The RiskTech Journal
Subscribe to get access now
The RTJ Bridge Subscription is a premier resource for executives and professionals focused on the intersection of risk management and technology. It provides subscribers with access to a curated collection of articles and expert insights designed to enhance risk management strategies through technological innovation. With its online format, The RTJ Bridge offers flexible access to critical information, helping leaders make informed decisions and stay competitive.

Why ROI Calculators Miss the Mark on IRM
Integrated risk management (IRM) is routinely forced into an ROI framing that does not fit its economic reality. ROI implies attributable incremental cash flows. Integrated risk management more often delivers dividends, meaning distributed benefits that improve enterprise outcomes without consolidating into a single return stream. This matters because many ROI calculators in market are not integrated risk management native.
The ROI calculators are commonly legacy GRC instruments, siloed by compliance use case, optimized for cost-of-compliance narratives, and weak at quantifying cross-domain integration value, loss mitigation value, and AI trust constraints. Public positioning reinforces this bias through language that centers measurement around the GRC program rather than enterprise-wide outcomes. AI amplifies the gap. As AI moves from feature to operating model, the trust dividend becomes a gating factor for scale. Standards and regulatory regimes increasingly emphasize trustworthiness, transparency, accountability, and information obligations.
What NVIDIA’s CES 2026 Post Signals for Autonomous IRM
NVIDIA’s January 5, 2026, CES post is not “just a chip announcement.” It is a blueprint for making agentic systems cheaper to run, faster to execute, more distributed (from data center racks to desktops and edge), and more simulation-driven. For Autonomous Integrated Risk Management (Autonomous IRM), the practical implication is that the limiting factor shifts. It becomes less about whether the enterprise can afford the compute and more about whether it can manage autonomous decision loops with bounded execution, reliable orchestration, and audit-grade evidence.
What changed (and why executives should care)
Cadence shifts: more risk work can run continuously rather than quarterly because inference economics and long-context performance are improving.
Scope expands: autonomy moves beyond cyber and compliance into operational resilience and “physical” validation patterns that rely on simulation and long-tail testing.
Expectations rise: decision provenance and replayable evidence become baseline requirements, not premium features.
What follows is the translation of NVIDIA’s CES announcements into Autonomous IRM implications, using an executive pattern: signal, why it matters, implication, program design change, and a measurable buyer proof point.

Does GRC Need Finishing School? The IRM Navigator™ View on Forrester’s GRC ‘Grad School’ Story
Forrester's recent blog “GRC Platforms Enter Their Grad School Era” contains a notable admission. The analysts describe GRC as "old enough to be in grad school," yet still struggling to prove it can act as the workhorse technology for modern risk professionals. After roughly 20 years of formal coverage, the firm suggests that GRC is not yet fully ready for the “real world” of risk and now needs a kind of graduate-level evolution, built on continuous controls monitoring, quantification, and AI. This observation raises an obvious question. Does GRC really need finishing school after decades of market evolution, or have we been asking the category to do the wrong job?

Agentic AI Moves From Hype to Operating Model: What Risk Leaders Must Do Now
EY’s newest global insight, “What Risk Leaders Need to Do Now About Agentic AI,” sets a clear challenge: organizations that treat agentic AI as another productivity initiative risk amplifying exposure, not mitigating it. The report argues that risk functions must now move beyond experimentation and build an enterprise operating model where autonomous and semi-autonomous agents can act safely, transparently, and in alignment with strategy.
This message reinforces a structural shift already underway in Integrated Risk Management (IRM). Wheelhouse Advisors’ Autonomous IRM model defines how these agentic systems should operate—not as isolated bots or chat interfaces, but as integrated decision engines that connect strategic intent, operational execution, and assurance validation.

Workiva’s Q3 2025 Results Signal the Rise of “Assured Data Platforms” in the IRM Market
Workiva’s Q3 2025 results represent more than a financial beat—they reveal a strategic inflection point for the Integrated Risk Management (IRM) market. The company delivered total revenue of $224 million, up 21% year over year, with subscription and support revenue growing 23%. Its non-GAAP operating margin expanded to 12.7%, nearly tripling from the prior year. Just as significant, customers with annual contract value (ACV) above $500,000 rose 42%, confirming enterprise-scale adoption of Workiva’s unified disclosure and assurance platform.
This growth underscores a broader market movement toward “assured data platforms”—solutions that unify financial, sustainability, and risk reporting within one governed architecture. As ESG regulation, audit digitization, and AI assurance converge, Workiva’s performance signals what IRM leaders should expect across the next phase of market maturity.

Technology Risk at Machine Speed: Why Integrated Systems Demand Integrated Risk Management
Jaguar Land Rover’s cyber incident shows how modern enterprises operate inside an interconnected matrix of risk. Technology assets and operational processes are closely linked, so a disruption in one tier quickly spreads across production sites, suppliers, dealers, and customers.
On September 2, 2025, JLR confirmed a cyber intrusion and proactively shut systems to contain the impact. By September 6, production was halted in the United Kingdom, Slovakia, Brazil, and India. West Midlands suppliers sent thousands of staff home. Dealer platforms, including the electronic parts catalogue, were inaccessible. Analysts estimate losses of £5 million per day, and insiders indicate recovery will take weeks rather than days. A group calling itself Scattered Lapsus$ Hunters claimed responsibility.

Audit Committees Signal a Mandate for Unified IRM, Not Just GRC
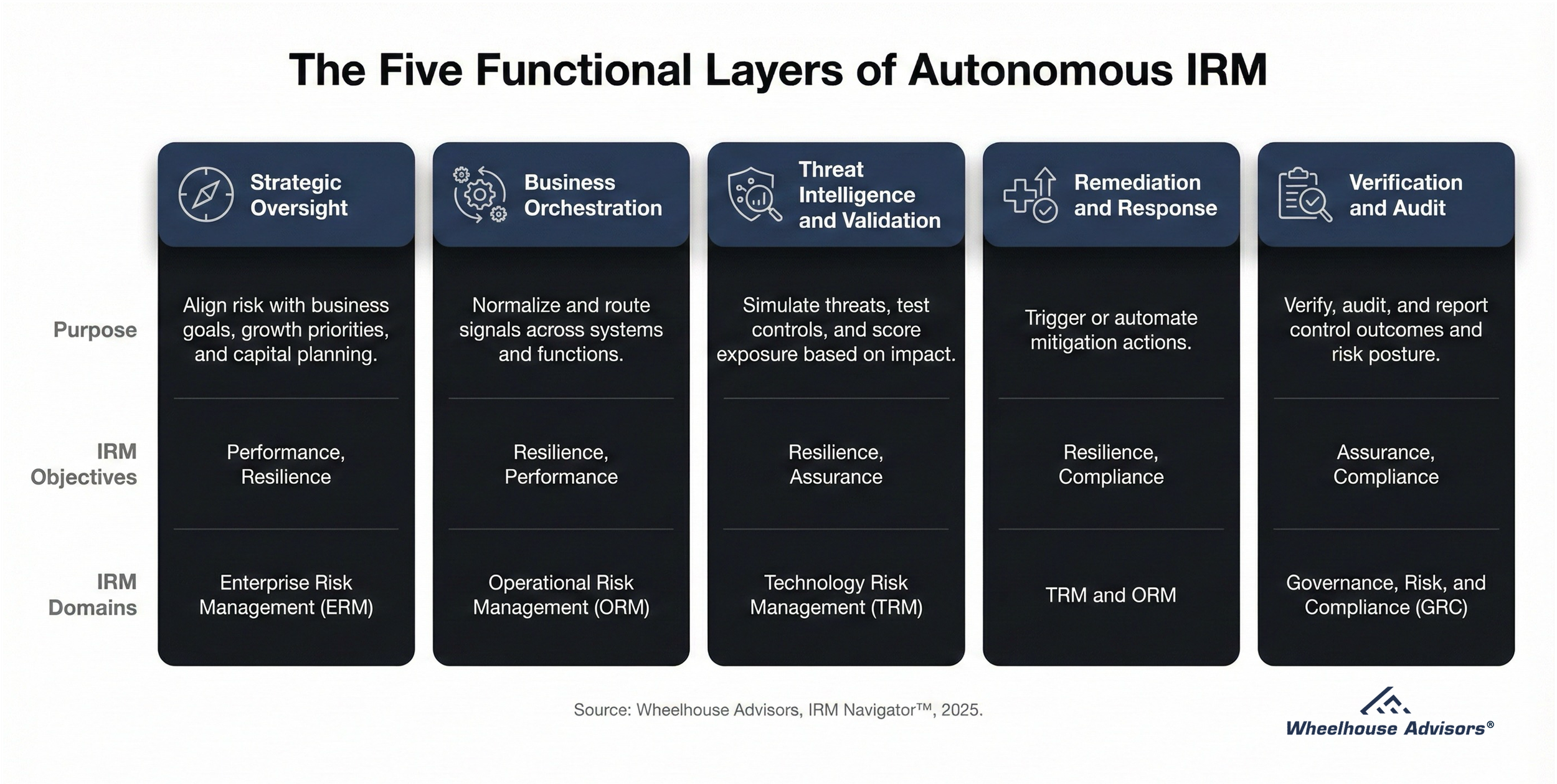
Audit committees in 2025 are under growing pressure to oversee risks that are more complex, interconnected, and fast-moving than ever before. KPMG’s survey of 85 U.S. audit committee members (February–May 2025) highlights systemic oversight gaps in cybersecurity, privacy, AI, and third-party resilience. While only one-quarter of respondents describe their risk management as holistic and forward looking, the survey reveals that committees are struggling less with awareness and more with execution. The IRM Navigator™ Maturity Curve confirms that most organizations remain in the early to mid stages of maturity. However, the five functional layers of Autonomous IRM offer a more practical blueprint for closing these oversight gaps and absorbing workload without restructuring committees.
This research note interprets the KPMG findings through the lens of both frameworks: the Maturity Curve, which shows where audit committees are today, and the five functional layers, which define how they can progress toward unified, assurance-driven oversight.

The Risk Ignored, Part II Chapter 5: The Academic Reckoning
In Part I of The Risk Ignored, we followed the rise and fall of GRC. Born in the aftermath of the Sarbanes-Oxley Act, it was codified by Archer, PwC, and Michael Rasmussen, and quickly became the acronym that defined a market. Yet by the late 2000s, GRC was collapsing under its own weight. The very acronym that promised coherence came to mean everything and, in practice, nothing at all.
The story of The Risk Ignored Part II: The Seeds of Integration begins here. The collapse of GRC and the inadequacy of compliance-first ERM created a void. The question, for both scholars and practitioners, was what comes next.

How IRM Can Protect Cyberinsurers from Cyberattacks
Cyberinsurance providers face a unique irony in today's risk landscape. Despite their role in safeguarding others against cyber threats, they have become prime targets for cybercriminals. Recent high-profile breaches, including attacks on Allianz Life, CNA Financial, and Philadelphia Indemnity, vividly illustrate this growing vulnerability. These incidents underscore not only the attractiveness of insurers as targets—given the extensive sensitive client data they hold—but also reveal substantial weaknesses in their ability to manage third-party risks, respond to incidents, and comply with tightening regulations.
If cyberinsurance companies fail to adopt a holistic, integrated approach to risk management, the resulting breaches may significantly damage their reputations, compromise their operational integrity, and erode market trust. It is therefore imperative to rethink their approach to cybersecurity risk management.

