How Integrated Risk Management Enables Cyber-ERM Convergence
Executive Summary
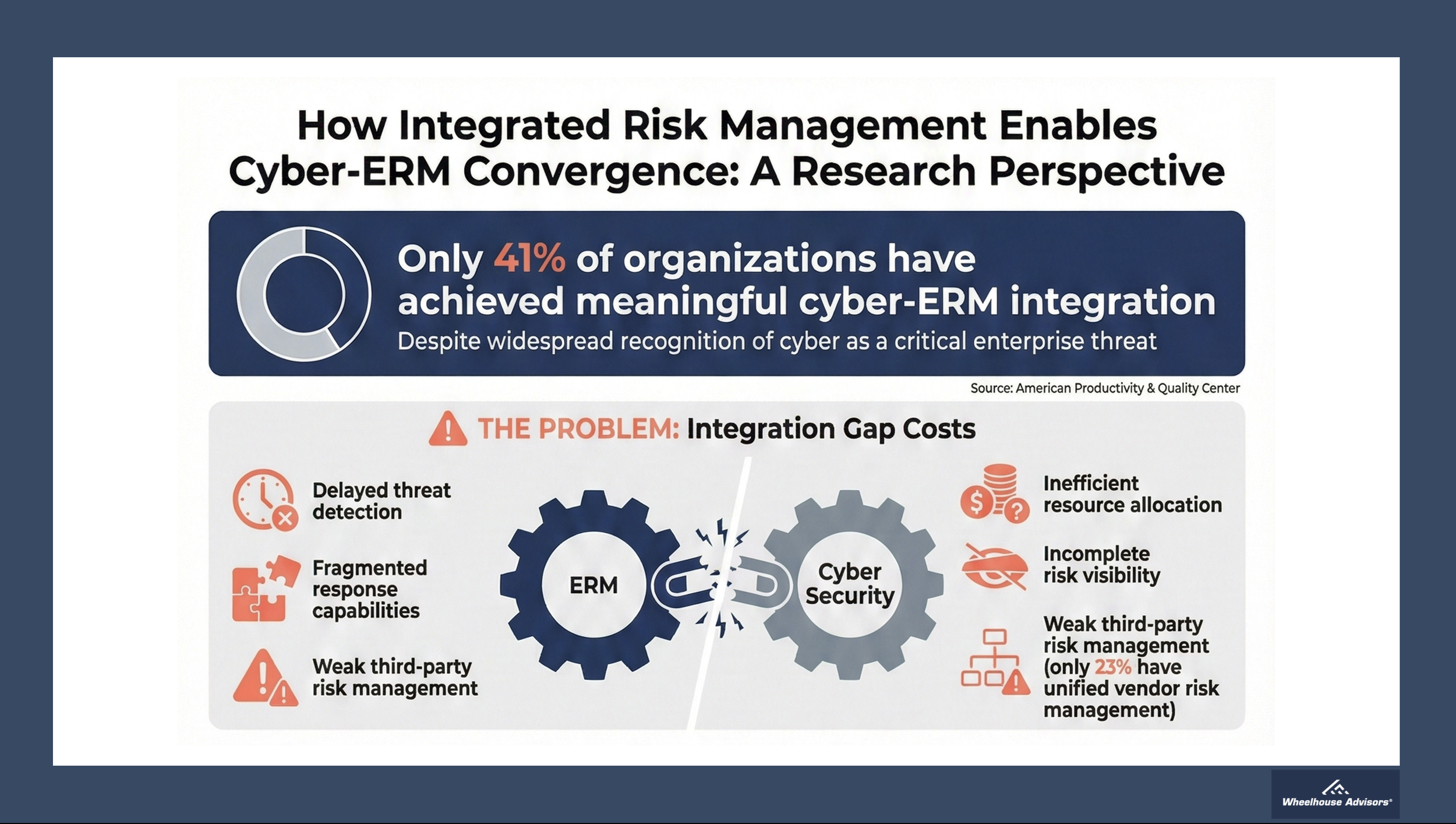
Recent research from the American Productivity & Quality Center reveals a sobering reality: only 41% of organizations have achieved meaningful integration between cybersecurity and enterprise risk management, and just 23% have unified third-party risk management. This gap persists despite widespread GRC platform adoption, revealing that compliance-first architectures cannot deliver the risk-first integration that cyber-ERM convergence requires. Integrated Risk Management provides the essential infrastructure to bridge this divide through its four-pillar framework: Performance, Resilience, Assurance, and Compliance.
Source: wheelhouseadvisors.com
The Problem: The Cyber-ERM Integration Gap
Cybersecurity teams typically operate in separate governance forums, use distinct measurement frameworks, and report through different organizational channels than ERM functions. This separation persists even as cyber incidents increasingly trigger cascading enterprise consequences affecting operations, financials, regulatory standing, and reputation.
The Evidence
Only 41% of organizations have achieved meaningful cyber-ERM integration
Just 23% have unified third-party risk management
Persistent separation of cyber risk reviews from ERM governance forums
Continued inability to frame cyber risks in financial terms supporting enterprise decisions
Source: American Productivity & Quality Center (APQC), 2025
The cost of fragmentation is substantial:
Delayed threat detection due to siloed information flows
Fragmented response capabilities when incidents occur
Inefficient resource allocation across overlapping risk functions
Incomplete risk visibility at the board and C-suite level
Weak third-party risk management, despite vendors’ growing role in breaches
Why Traditional GRC Falls Short
The 41% integration rate disproves a common assumption: that traditional Governance, Risk, and Compliance platforms provide the unified governance structure needed to close the integration gap. Many organizations have deployed GRC platforms, yet meaningful cyber-ERM integration remains elusive. This disconnect reveals fundamental architectural limitations.
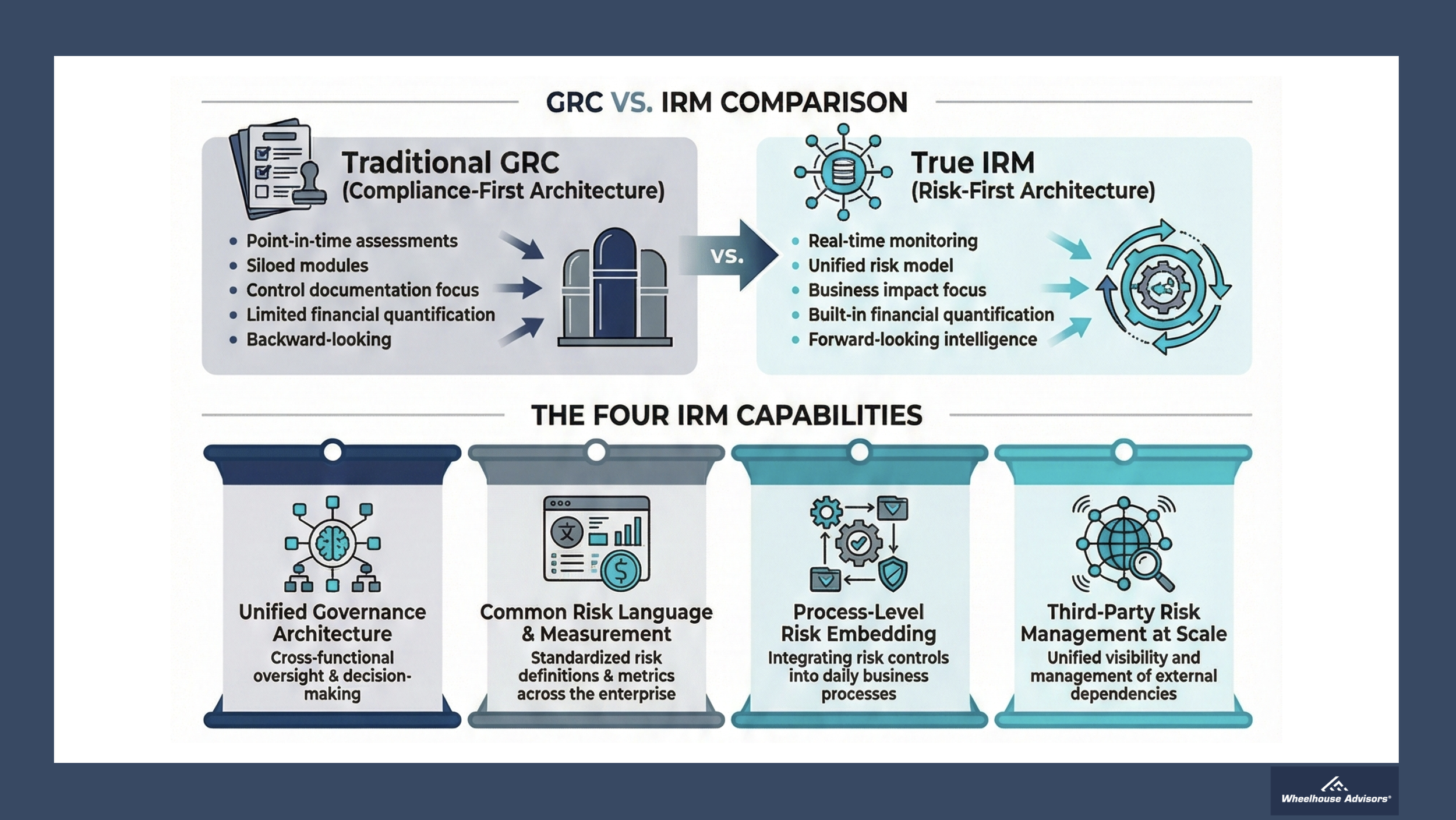
GRC: Compliance-First Architecture
Traditional GRC platforms emerged primarily to manage compliance obligations and audit workflows. This heritage creates three critical limitations that prevent cyber-ERM convergence.
1. Point-in-Time Assessments vs. Continuous Monitoring
GRC Limitation:
GRC platforms optimize for periodic assessments and audit cycles. Risk snapshots become stale between assessment periods. Cyber risks evolve faster than GRC assessment schedules. The temporal mismatch between cyber incident velocity and enterprise risk reporting cadence creates blind spots.
Business Impact:
Boards review outdated cyber risk profiles. Organizations base response plans on yesterday’s threat landscape. Resource allocation decisions lag threat evolution.
2. Siloed by Domain vs. Enterprise-Wide Integration
GRC Limitation:
Modular architecture means separate implementations for cyber, operational risk, and compliance. Limited cross-module integration creates disconnected risk views. Each domain maintains its own taxonomies, metrics, and governance processes. Third-party risk management sits isolated from vendor operational dependencies.
Business Impact:
Cybersecurity and ERM teams speak different risk languages. No unified view of how cyber risks affect strategic objectives exists. Vendor cyber assessments remain disconnected from procurement and supplier management. CFOs cannot compare cyber investments against other enterprise priorities.
3. Manual Financial Quantification vs. Built-In Financial Translation
GRC Limitation:
Compliance-centric data models track controls, not business impacts. No native capability exists to quantify cyber risks in financial terms. Technical risk scores don’t translate to CFO-level decision support. Cyber risk remains in IT language rather than business language.
Business Impact:
Cyber risks get excluded from enterprise risk portfolios requiring financial comparability. CFOs cannot evaluate cybersecurity ROI against other capital allocation options. Boards lack financial context to prioritize cyber investments. Organizations cannot integrate cyber risk into financial planning and reporting.
Source: wheelhouseadvisors.com
The Evidence: Why Organizations With GRC Still Lack Integration
The research findings validate GRC’s limitations empirically. If GRC platforms effectively enabled cyber-ERM integration, organizations with mature GRC deployments would show high integration rates. Instead:
Only 41% achieve meaningful cyber-ERM integration across a broad sample that includes many GRC users
Just 23% apply unified risk management to third parties, despite vendor risk serving as a core GRC use case
Cyber risk reviews remain separate from ERM governance forums, even in GRC-enabled organizations
Organizations still cannot frame cyber risks in financial terms that support enterprise decisions
These outcomes don’t represent failures of GRC platforms to execute their intended purpose. They provide evidence that compliance-oriented architectures cannot deliver the risk-first integration that cyber-ERM convergence requires.
The Integration Trap: Speed Without Decision Authority
Recent research on board priorities reveals a dangerous pattern: the Integration Trap. This trap occurs when organizations accelerate the flow of data and automation without the corresponding ability to interpret signals or assign decision rights.
Organizations pursuing cyber-ERM integration face a specific manifestation of this trap. GRC platforms can successfully aggregate cyber risk data alongside other enterprise risks, creating unified dashboards and consolidated reports. This produces visibility without control. Everyone can see the cyber risk, but no one is empowered to act decisively because decision rights, response protocols, and escalation pathways remain siloed.
The result is what many organizations already experience: signals without decisions. Cyber incidents are detected faster, risk metrics update in real-time, and alerts proliferate across integrated systems. Yet response authority, accountability, and execution protocols remain unchanged. Decision latency increases precisely when speed matters most.
This integration trap explains why 41% integration statistics persist despite widespread technology investment. Organizations are building high-speed highways for cyber risk data without traffic lights, without the decision architecture that transforms visibility into action. Integration without risk discipline amplifies risk rather than containing it.
The “Integrated GRC” Mirage: Integration Trap for Compliance
The market has responded to integration demands with a new category: integrated GRC. Major vendors position their offerings as integrated solutions that promise unified governance, risk, and compliance management.
However, examining vendor architectures reveals a consistent pattern. Most integrated GRC platforms represent integration within the Assurance and Compliance pillars only. They connect internal audit, regulatory compliance, ethics programs, policy management, and SOX controls into unified workflows. This is valuable, but it’s not cyber-ERM integration. It’s compliance module integration, linking different compliance and assurance functions together while leaving Performance and Resilience pillars disconnected.
The vendor marketing consistently focuses on connecting board management, policy administration, compliance monitoring, internal audit, and entity management. The integration optimizes second-line and third-line assurance functions, not first-line operations. Connected workflows eliminate silos between compliance functions while leaving operational silos intact.
This creates the Integration Trap for GRC. Organizations deploy integrated GRC platforms, achieve consolidated compliance dashboards, and assume they’ve solved the cyber-ERM integration challenge. In reality, they’ve only integrated compliance-related activities with each other. Cybersecurity remains isolated in TRM, operational resilience stays in ORM, and strategic risk management sits in ERM, all disconnected from the integrated GRC platform.
The consequences mirror the broader Integration Trap pattern:
Faster compliance reporting without faster incident response
Unified compliance dashboards without unified decision authority
Consolidated audit findings without coordinated remediation across ORM/TRM/GRC
Better governance visibility without better operational resilience
Eliminated redundant assessments between second-line functions while first-line operations remain blind to second-line insights
Organizations believe they’ve integrated cyber and ERM because their GRC platform shows both types of risks on the same dashboard. But when a cyber incident occurs, the integration illusion shatters. Response authority remains fragmented across IT, operations, compliance, and governance. The platform integrated the compliance data but not the decision rights, integrated the risk assessments but not the response protocols, integrated the audit findings but not the remediation execution.
This is why integrated GRC cannot deliver cyber-ERM convergence. True integration requires all four IRM pillars working together, not just better integration within Assurance and Compliance pillars. When vendors claim to solve integration by connecting 20+ compliance modules or enabling seamless collaboration, they’re creating a false sense of security that leaves fundamental operational silos intact. The compliance and assurance functions are integrated, but the business remains fragmented.
A forthcoming RTJ Bridge research note will examine the Integration Trap for GRC phenomenon in greater depth, analyzing how the integrated GRC market positioning creates visibility without control across the vendor landscape.
Source: wheelhouseadvisors.com
The IRM Solution: Risk-First Architecture
Source: wheelhouseadvisors.com
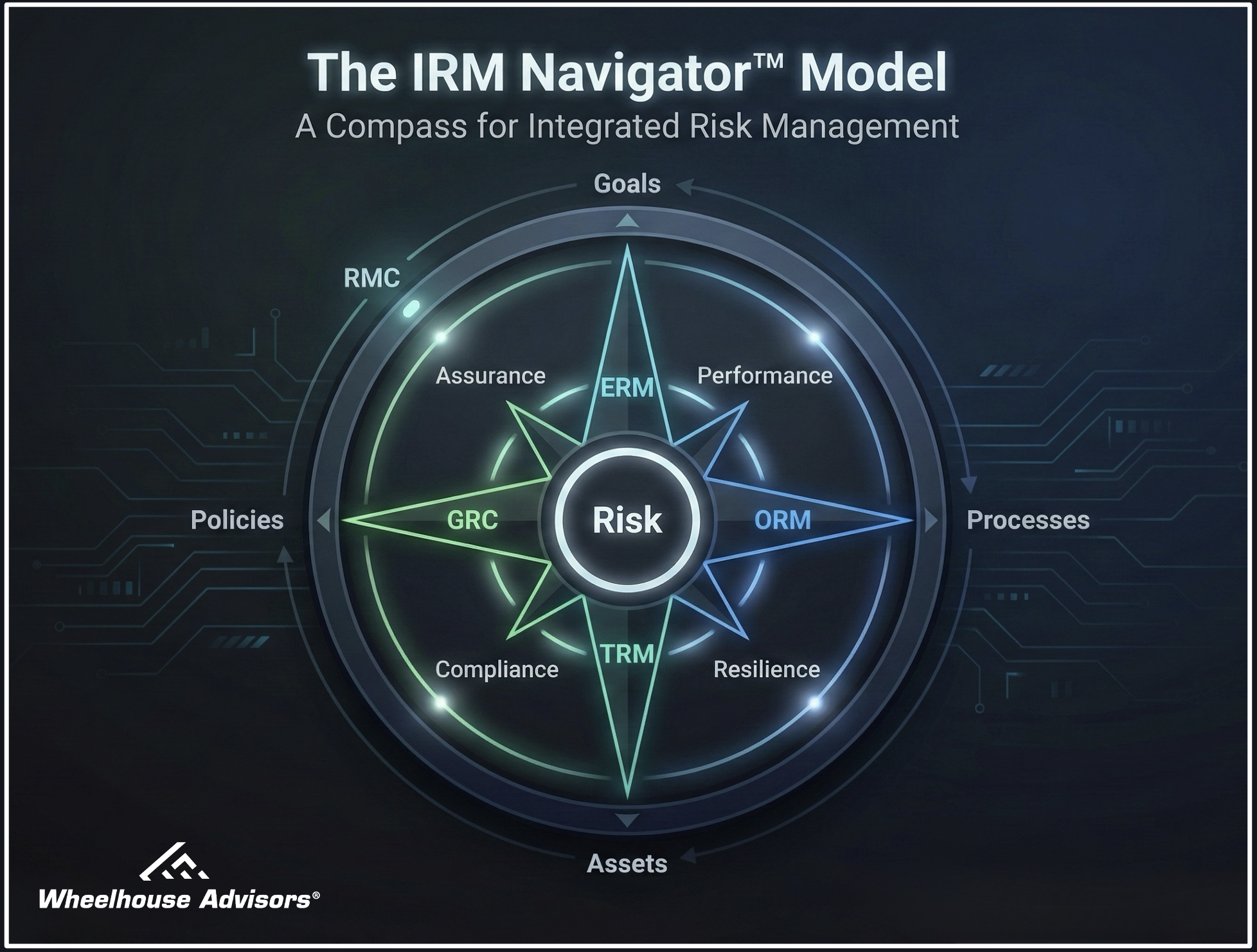
Integrated Risk Management platforms and frameworks directly address the structural barriers preventing cyber-ERM convergence. The IRM Navigator Model provides the comprehensive framework that distinguishes organizations with strong cyber-ERM integration.
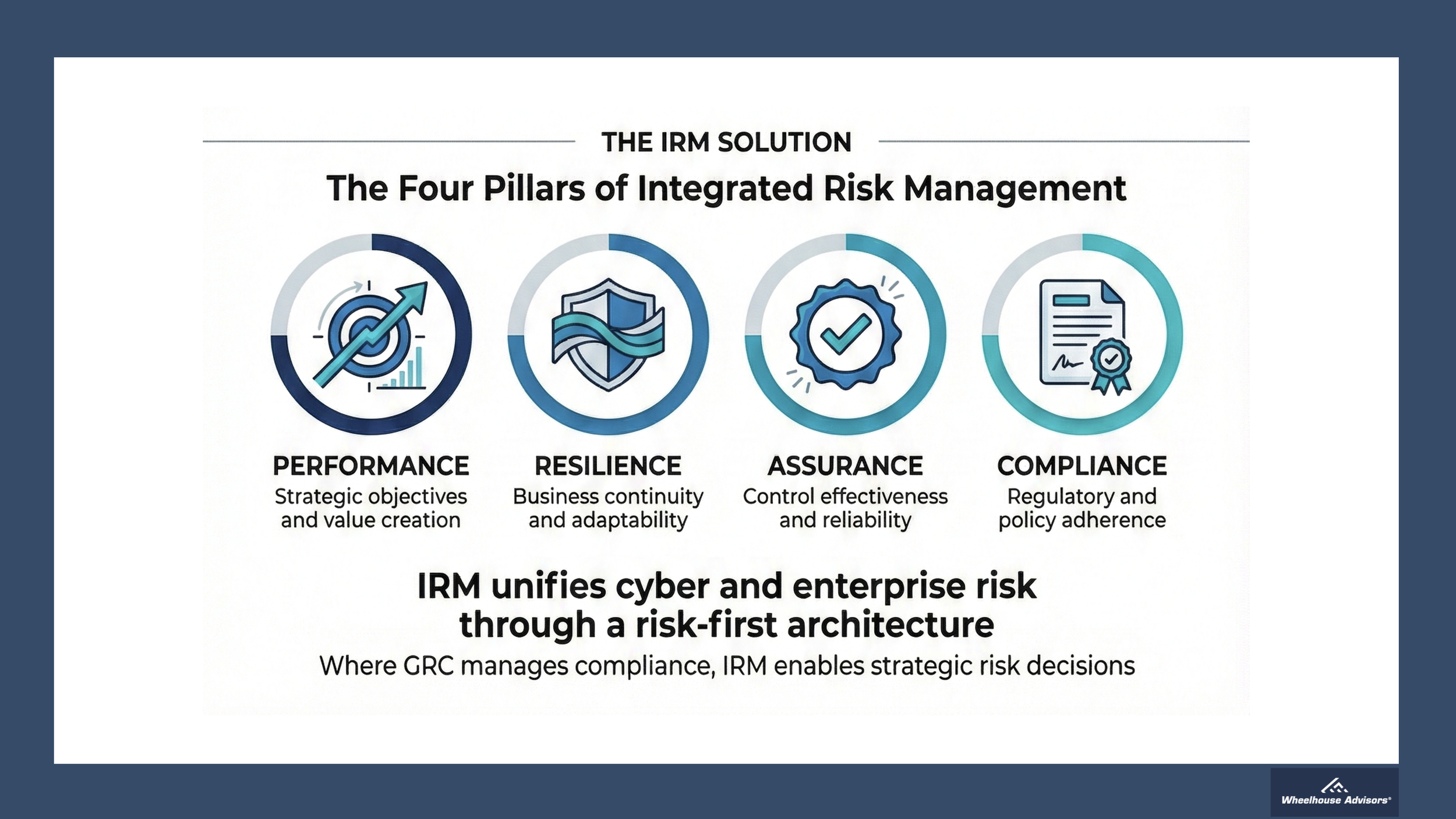
The Four Pillars of Integrated Risk Management
IRM organizes around four fundamental pillars that encompass all dimensions of enterprise risk:
1. PERFORMANCE: Strategic Objectives and Value Creation
The Performance pillar represents the strategic and operational excellence dimension of IRM. Organizations use it to achieve business objectives and create value while managing operational execution.
This pillar encompasses board risk oversight and strategic risk management, corporate governance and enterprise legal frameworks, insurance and claims management, ESG and sustainability risk, and environmental, health, and safety risk.
For cyber-ERM integration, the Performance pillar ensures organizations evaluate cyber risks in the context of both strategic objectives and operational execution. When CFOs assess cybersecurity investments through the Performance lens, they can determine whether cyber risk mitigation supports or impedes strategic goals while also considering operational impacts like business interruption and insurance implications.
2. RESILIENCE: Business Continuity and Adaptability
The Resilience pillar addresses the organization’s ability to maintain operations and adapt to disruption across both operational and technology domains.
This pillar spans business continuity and disaster recovery, supplier and third-party risk management, cybersecurity and information technology risk, information technology risk management, and digital and operational technology risk.
The Resilience pillar is where cyber-ERM integration becomes most tangible. Cybersecurity sits at the intersection of operational resilience (business continuity, vendor risk) and technology resilience (IT infrastructure, disaster recovery). This integration transforms cyber from an IT problem into an enterprise resilience issue, directly addressing the research finding that organizations with strong integration embed cyber risk into business processes.
3. ASSURANCE: Control Effectiveness and Reliability
The Assurance pillar provides confidence that organizations manage risks appropriately and that controls operate effectively across both strategic and compliance dimensions.
This pillar includes board risk oversight and enterprise governance, internal audit functions, regulatory compliance, ethics and conduct programs, and policies and procedures management.
The Assurance pillar explains why traditional GRC platforms, while valuable, prove insufficient for cyber-ERM integration. GRC provides compliance assurance but requires the enterprise risk governance overlay to connect controls to strategic objectives. By positioning GRC alongside ERM within the Assurance pillar, organizations can leverage compliance capabilities while also providing board-level governance and strategic risk oversight.
4. COMPLIANCE: Regulatory and Policy Adherence
The Compliance pillar ensures adherence to regulatory requirements and technology standards while managing the governance of technology risk.
This pillar covers regulatory compliance management, policies and procedures, cybersecurity standards and frameworks, information technology compliance, and digital and AI governance.
The Compliance pillar addresses a critical gap in cyber-ERM integration: the connection between regulatory compliance obligations and technology risk management practices. Organizations often manage GRC compliance separately from technology standards and cybersecurity frameworks. This pillar unites them, ensuring that technology governance meets both regulatory requirements and operational security needs.
How the Four Pillars Enable Cyber-ERM Convergence
The IRM Navigator Model’s four pillars create the structural conditions for cyber-ERM integration through several mechanisms.
1. Unified Governance Structure
Rather than maintaining separate governance forums for cyber (typically under IT or security) and enterprise risk (typically under the CRO or CFO), IRM establishes integrated risk councils that evaluate all risks within the same governance framework. The Performance pillar provides board-level oversight, while the Assurance pillar ensures effective control implementation across all domains.
Critically, IRM’s governance model addresses the Integration Trap by explicitly defining decision rights alongside data flows. Unified governance means not just consolidated reporting but coordinated authority. When a cyber risk materializes, the framework specifies who holds decision authority, what actions are preauthorized, and how escalation proceeds. This transforms integration from visibility exercise into decision advantage.
2. Common Risk Language and Measurement
The four-pillar framework creates a shared vocabulary where cyber risks are described using the same terminology and metrics as other enterprise risks. A cyber incident isn’t just a security breach but rather a Performance risk (potential impact on strategic objectives), a Resilience risk (operational disruption and recovery), an Assurance risk (control failure requiring remediation), and a Compliance risk (regulatory reporting and governance).
This multidimensional view enables the financial quantification that the research identifies as critically absent in most organizations.
3. Process-Level Risk Embedding
The Resilience pillar’s focus on operational and technology risk management enables IRM to embed cyber controls directly into business processes. When organizations manage cyber as part of ORM and TRM rather than as a separate IT function, security controls integrate with process controls, workflow automation, and business application governance.
4. Third-Party Risk Management at Scale
With only 23% of organizations applying unified risk management to suppliers and partners, third-party risk remains a critical weak point. The IRM Navigator Model addresses this through the Resilience pillar, which explicitly includes supplier and third-party risk management. This positions vendor cyber risk assessment alongside other supplier risks (quality, financial stability, ESG compliance), enabling the consistent due diligence that research shows most organizations lack.
Why the Four-Pillar Model Succeeds Where GRC Fails
The IRM Navigator Model reveals why traditional GRC platforms cannot deliver cyber-ERM integration. GRC appears in two pillars (Assurance and Compliance) but always pairs with other solution areas. Organizations that rely on GRC alone miss the critical ERM, ORM, and TRM components that enable true integration.
True integration requires all four pillars working together. Performance connects risks to strategic objectives and operational execution. Resilience embeds risk management into operations and technology. Assurance provides board governance and compliance verification. Compliance ensures regulatory adherence and technology governance.
Notice that cybersecurity and technology risk appear in both Resilience and Compliance pillars, while ERM appears in both Performance and Assurance. This cross-pillar integration enables cyber-ERM convergence. When CFOs leverage IRM to anchor cyber discussions within this four-pillar framework, cyber risk naturally integrates with enterprise risk because the architecture demands it.
Source: wheelhouseadvisors.com
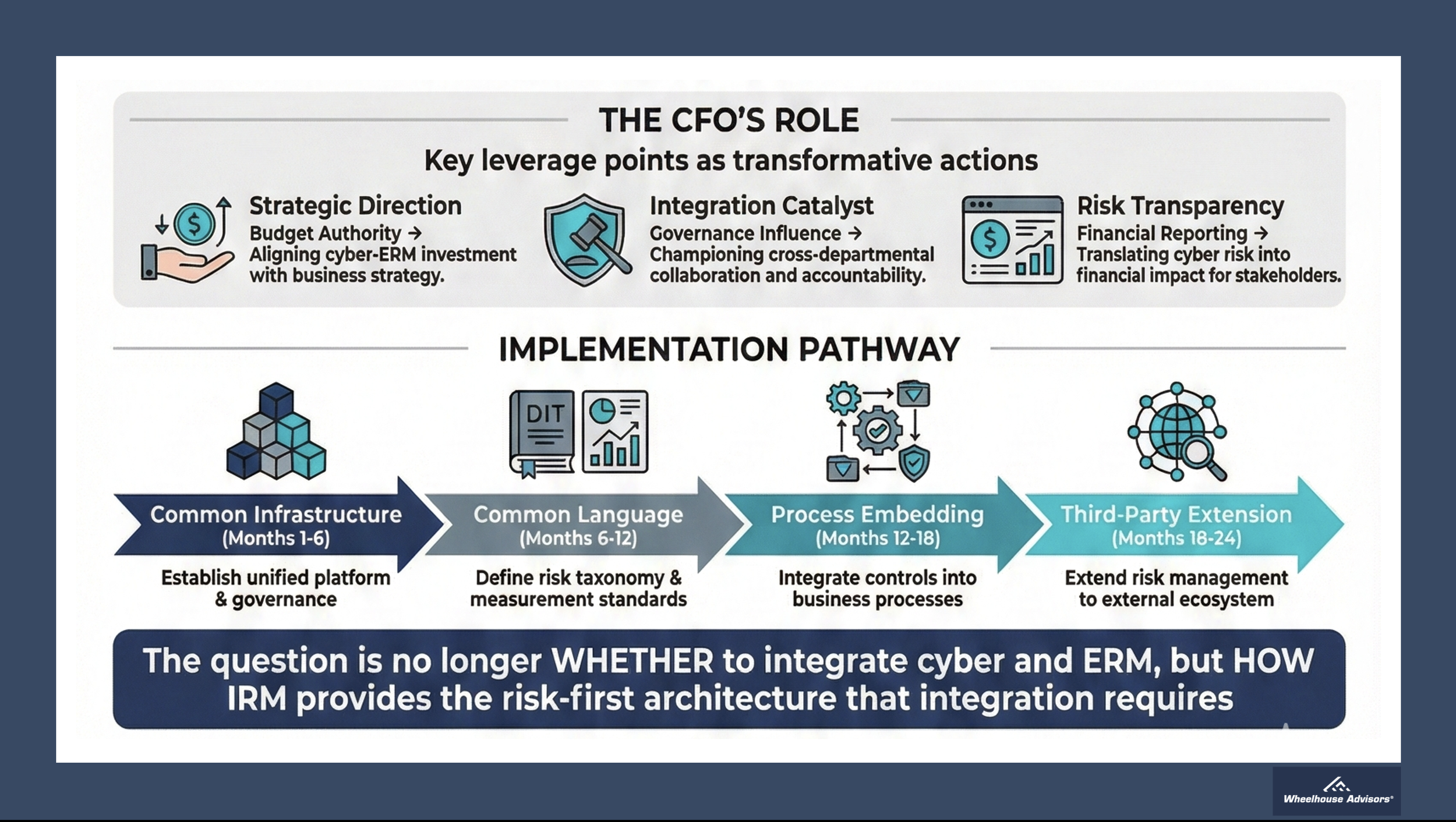
The CFO’s Strategic Role in IRM-Enabled Integration
The research from APQC and CFO.com highlights CFOs as uniquely positioned to drive cyber-ERM integration due to three sources of organizational authority: budget control, governance influence, and financial reporting obligations. When IRM platforms empower CFOs, they can leverage these authorities to mandate the integration that compliance-first GRC platforms cannot deliver. IRM enables CFOs to model ROI of security investments against quantified risk reduction, compare cyber risk mitigation options against other capital allocation priorities, require consistent risk reporting frameworks across all functions, integrate cybersecurity controls into SOX compliance frameworks, and demand real-time visibility into cyber risks affecting financial reporting.
Conclusion
The 41% cyber-ERM integration rate and the 23% third-party risk integration rate reveal that current approaches have failed. Traditional GRC platforms, despite their value for compliance management and audit workflows, cannot bridge the cyber-ERM gap due to three fundamental architectural limitations: point-in-time assessments rather than continuous monitoring, siloed by domain rather than enterprise-wide integration, and manual financial quantification rather than built-in financial translation.
Organizations don’t face implementation failures. They confront architectural constraints inherent to compliance-first platforms.
IRM’s risk-first architecture, organized around four pillars (Performance, Resilience, Assurance, Compliance), provides the structural foundation that enables cyber-ERM convergence. By embedding cyber risk management within operational resilience, connecting it to strategic objectives, ensuring board governance, and unifying technology and regulatory compliance, IRM transforms cyber risk from an isolated IT concern into an integrated enterprise capability.
The path forward is clear. Organizations seeking to close the cyber-ERM integration gap must move beyond compliance-oriented GRC platforms and embrace comprehensive IRM frameworks. Where GRC manages compliance, IRM enables strategic risk decisions. The choice is no longer between tools but between architectural approaches: compliance-first or risk-first. Only the latter can deliver the integration that boards, CFOs, and CISOs increasingly demand.
References
American Productivity & Quality Center (APQC). (2025). Cyber-ERM Integration Research Study. Retrieved from CFO.com article “What CFOs can do to close the cyber-ERM integration gap” (February 2025).
Wheelhouse Advisors. (2026). Board Priorities 2026: The Integration Trap. The RiskTech Journal.
Wheelhouse Advisors. (2025). IRM Navigator™ Viewpoint Report - 2025 Edition.
Wheelhouse Advisors. (2025). IRM Navigator™ Vendor Compass for Governance, Risk and Compliance - 2025 Edition.
Wheelhouse Advisors. (2025). IRM Navigator™ Vendor Compass for Technology Risk Management - 2025 Edition.
Wheelhouse Advisors. (2023-2025). The RiskTech Journal.
Wheelhouse Advisors. (July 15, 2025). Risk Management Technology Market Reaches $61.6 Billion as Wheelhouse Advisors Launches 2025-2026 IRM Navigator™ Report Series [Press release]. PRWeb.